Admin-access: Difference between revisions
(Created page with "<span id="admin-access"></span> = Admin Access = The Admin Access menu contains settings for who is allowed to administer the router and access the network, how those users connect, and more. The Admin Access menu is divided into sections. These sections include Web Admin, SSH Daemon, Telnet Daemon, Admin Restrictions and Username/Password. <span id="web-admin"></span> == Web Admin == The Web Admin section has settings to control who can access FreshTomato's web inter...") |
No edit summary |
||
| (3 intermediate revisions by the same user not shown) | |||
| Line 7: | Line 7: | ||
== Web Admin == | == Web Admin == | ||
The Web Admin section has settings to control who can access | The Web Admin section has settings to control who can access Tomato64's web interface, how, and from where. It also allows you to choose which menus stay nested or shown. Finally, it also has settings for the web interface's color scheme.<br /> | ||
'''Local Access: '''This let you choose which web protocol(s) are allowed to communicate with the web interface via the LAN.<br /> | |||
Port and Wireless access options will appear, depending on which selection you choose. | Port and Wireless access options will appear, depending on which selection you choose. | ||
* Disabled - Choosing this disables all LAN access to | * Disabled - Choosing this disables all LAN access to Tomato64's web interface via web protocols. | ||
* HTTP - Choosing this allows LAN Ethernet clients to access the web interface via the HTTP protocol. | * HTTP - Choosing this allows LAN Ethernet clients to access the web interface via the HTTP protocol. | ||
** HTTP Port - Here, enter the port number on which you want HTTP administration traffic to flow. (Default: 80). | ** HTTP Port - Here, enter the port number on which you want HTTP administration traffic to flow. (Default: 80). | ||
| Line 26: | Line 26: | ||
<br /> | <br /> | ||
[[File:4e4da6cb5f7e051296ee8f22e59e4600.png|frame|none]] | |||
<br /> | <br /> | ||
| Line 34: | Line 34: | ||
=== SSL Certificate === | === SSL Certificate === | ||
'''Common Name (CN): '''Here, enter the human-friendly name of the SSL web administrative certificate you wish to generate. | |||
'''Regenerate:'''TBD. | |||
'''Save in NVRAM: '''TBD. | |||
'''Remote Access:''' This lets you choose whether and how a user can remotely access | '''Remote Access:''' This lets you choose whether and how a user can remotely access Tomato64's web interface. | ||
* Disabled - This prevents all access to | * Disabled - This prevents all access to Tomato64's web interface via the WAN port/Internet.<br /> | ||
Only LAN clients will be able to access the web interface. For security reasons, this is<br /> | Only LAN clients will be able to access the web interface. For security reasons, this is<br /> | ||
the default and recommended setting. | the default and recommended setting. | ||
* HTTP - This allows web access to | * HTTP - This allows web access to Tomato64's WAN interface/Intenet via the<br /> | ||
HTTP web protocol. | HTTP web protocol. | ||
* HTTPS - This allows web access to | * HTTPS - This allows web access to Tomato64's WAN interface/Internet via the<br /> | ||
HTTPS (SSL-encrypted web) secure protocol. | HTTPS (SSL-encrypted web) secure protocol. | ||
| Line 74: | Line 74: | ||
== SSH Daemon == | == SSH Daemon == | ||
Secure SHell is a tunneling protocol that allows you to make secure local and remote connections to the | Secure SHell is a tunneling protocol that allows you to make secure local and remote connections to the Tomato64 router. With the help of the Dropbear service, it also allows you to make SSH connections ''though ''the router, to LAN client devices. Setings in this section let you enable or disable the SSH Daemon and the Dropbear daemon, and configure their operation. | ||
'''Enable at Startup:''' Checking this starts the SSH Daemon when the router boots. (Default: Enabled). | '''Enable at Startup:''' Checking this starts the SSH Daemon when the router boots. (Default: Enabled). | ||
| Line 81: | Line 81: | ||
<br /> | <br /> | ||
[[File:08f771d238b7c8643a5745335ef29a2e.png|frame|none]] | |||
<br /> | <br /> | ||
'''Remote Access:''' Checking this allows SSH connections from remote WAN/Internet clients. (Default: Disabled). | '''Remote Access:''' Checking this allows SSH connections from remote WAN/Internet clients. (Default: Disabled). | ||
'''Remote Forwarding: '''Checking this enables the Dropbear service. This service/daemon provides SSH services on the router and supports SSH port tunneling/forwarding. Do not confuse this with standard (local) Port Forwarding. | |||
For example, let's say you want to be able to access a Windows PC on your LAN via Remote Desktop, but you don't want the security risk of opening up a port for RDP to the Internet via standard Port Forwarding. Instead, you can make an SSH connection into the router with an SSH port tunnel/forward configured (example: 127.0.0.1:1234 gets tunnelled/forwarded through SSH to 192.168.1.66:3389. This way, when you're connected via SSH to the router, you can open up RDP on the machine running the SSH client, and connect to 127.0.0.1:1234 and you're securely connected to 192.168.1.66 on your LAN. All traffic flows through SSH, and thus is encrypted. (RDP already uses encryption, but it's weaker than that provided by SSH). | For example, let's say you want to be able to access a Windows PC on your LAN via Remote Desktop, but you don't want the security risk of opening up a port for RDP to the Internet via standard Port Forwarding. Instead, you can make an SSH connection into the router with an SSH port tunnel/forward configured (example: 127.0.0.1:1234 gets tunnelled/forwarded through SSH to 192.168.1.66:3389. This way, when you're connected via SSH to the router, you can open up RDP on the machine running the SSH client, and connect to 127.0.0.1:1234 and you're securely connected to 192.168.1.66 on your LAN. All traffic flows through SSH, and thus is encrypted. (RDP already uses encryption, but it's weaker than that provided by SSH). | ||
'''Port: '''Here, enter the port number on which SSH traffic will flow. Changing the port from the default is highly recommended. Port 22 is constantly scanned by Internet hackers. (Default: 22). | |||
'''Allow Password Login: '''Checking this allows clients to login via SSH with only the normal administrative username and password. No authorized encryption key is needed. When disabled, SSH will require an authorized key to allow a client to log on. | |||
'''Authorized Keys:''' Here enter one or more encryption keys which authorize an SSH client to access to the LAN. | '''Authorized Keys:''' Here enter one or more encryption keys which authorize an SSH client to access to the LAN. | ||
| Line 103: | Line 103: | ||
(Terminal EmuLation over the NEtwork) is a protocol which allows LAN and remote connections via a command-line interface. Unlike SSH, Telnet is not a secure protocol. | (Terminal EmuLation over the NEtwork) is a protocol which allows LAN and remote connections via a command-line interface. Unlike SSH, Telnet is not a secure protocol. | ||
'''Enable at Startup:''' Checking this enables the Telnet Daemon, allowing connections to | '''Enable at Startup:''' Checking this enables the Telnet Daemon, allowing connections to Tomato64 via Telnet. | ||
'''Port:''' Here, you can enter the port number on which Telnet connections will be made to the router. (Default: 23). | '''Port:''' Here, you can enter the port number on which Telnet connections will be made to the router. (Default: 23). | ||
'''Stop Now / Start Now. '''Clicking this button immediately stops the Telnet Daemon. The Telnet daemon will restart at the next reboot (if Enable at Startup is checked). When the Telnet Daemon has stopped, this button will change to read "Start Now". Clicking Start Now immediately starts the Telnet Daemon. When Telnet is finished starting, the text on this button will change back to "Stop Now". | |||
<br /> | <br /> | ||
[[File: | [[File:8df69e6c26ffe04b52fd742f27ad1a3a.png|frame|none]] | ||
<span id="admin-restrictions"></span> | <span id="admin-restrictions"></span> | ||
| Line 117: | Line 117: | ||
'''Allowed Remote IP Address:''' Here, you can specify the IP addresses or DNS names of hosts you want to allow to connect to the Tomato router's web aministration interface. Addresses can be individual, separated with commas, or a range separated by a dash, such as 1.1.1.1-2.2.2.2 . This setting applies to local and remote administration via HTTP, HTTPS, SSH (if enabled) and Telnet (if enabled). | '''Allowed Remote IP Address:''' Here, you can specify the IP addresses or DNS names of hosts you want to allow to connect to the Tomato router's web aministration interface. Addresses can be individual, separated with commas, or a range separated by a dash, such as 1.1.1.1-2.2.2.2 . This setting applies to local and remote administration via HTTP, HTTPS, SSH (if enabled) and Telnet (if enabled). | ||
'''Limit Connection Attempts: '''Here, you can specify whether you want SSH or Telnet connection attempts to be limited to a certain number of attempts (n) at a certain frequency (f). (Default: 3 connection attempts allowed every 60 seconds). | |||
Checking SSH limits the number of SSH connection attempts to number n at frequency f (in seconds). Checking Telnet limits the number of Telnet connection attempts to number n at frequency s (in seconds). | Checking SSH limits the number of SSH connection attempts to number n at frequency f (in seconds). Checking Telnet limits the number of Telnet connection attempts to number n at frequency s (in seconds). | ||
<br /> | <br /> | ||
[[File:A7c2f09179ae06e42debf184f16c60aa.png|frame|none]] | |||
<span id="usernamepassword"></span> | <span id="usernamepassword"></span> | ||
| Line 129: | Line 129: | ||
You are strongly urged to change these from the default settings to keep the router and network secure. | You are strongly urged to change these from the default settings to keep the router and network secure. | ||
'''Username:''' Here, enter the | '''Username:''' Here, enter the Tomato64 logon Username you wish to set. Leaving this field empty sets the username as "root". (Default: "root"). | ||
'''Password:''' Here, enter the | '''Password:''' Here, enter the Tomato64 logon password you wish to set. (Default: "admin"). | ||
'''Re-enter to confirm:''' In this field, enter the password again to confirm it is correct. The password will be changed only when the text entered in this field and in the Password field match exactly. | '''Re-enter to confirm:''' In this field, enter the password again to confirm it is correct. The password will be changed only when the text entered in this field and in the Password field match exactly. | ||
<br /> | <br /> | ||
[[File: | [[File:39f890aeb648c15c4715402a590e36a0.png|frame|none]] | ||
<br /> | <br /> | ||
<br /> | <br /> | ||
Latest revision as of 07:07, 30 September 2023
Admin Access
The Admin Access menu contains settings for who is allowed to administer the router and access the network, how those users connect, and more. The Admin Access menu is divided into sections. These sections include Web Admin, SSH Daemon, Telnet Daemon, Admin Restrictions and Username/Password.
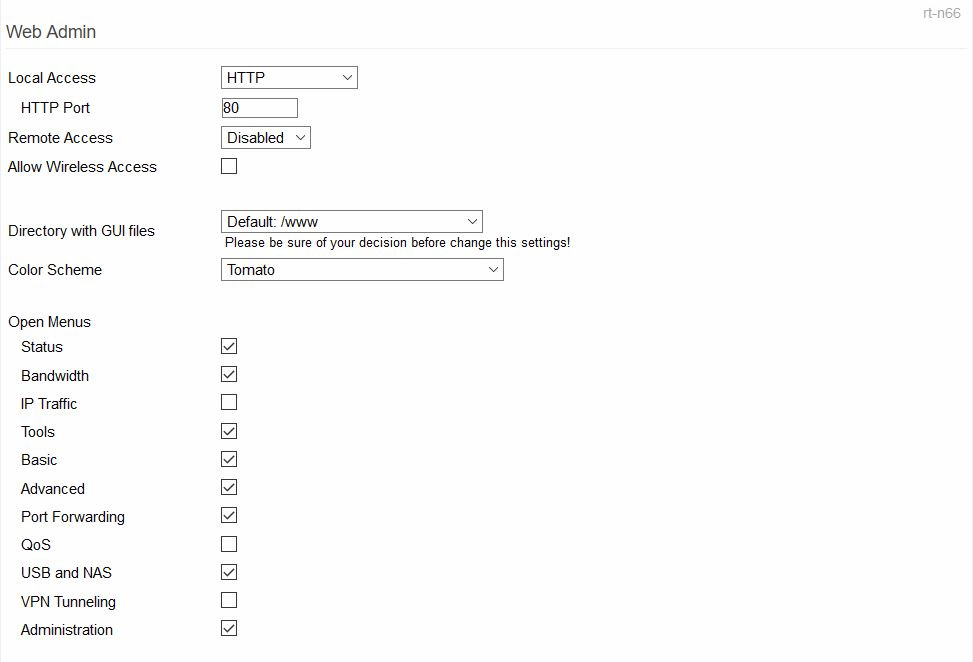
Web Admin
The Web Admin section has settings to control who can access Tomato64's web interface, how, and from where. It also allows you to choose which menus stay nested or shown. Finally, it also has settings for the web interface's color scheme.
Local Access: This let you choose which web protocol(s) are allowed to communicate with the web interface via the LAN.
Port and Wireless access options will appear, depending on which selection you choose.
- Disabled - Choosing this disables all LAN access to Tomato64's web interface via web protocols.
- HTTP - Choosing this allows LAN Ethernet clients to access the web interface via the HTTP protocol.
- HTTP Port - Here, enter the port number on which you want HTTP administration traffic to flow. (Default: 80).
- Allow Wireless Access - Checking this lets LAN WiFi clients access the web interface. (Default: enabled).
- HTTPS - Choosing this allows LAN Ethernet clients to access the web interface via the HTTPS (SSL-encrypted web) protocol.
- HTTPS port: Here, enter the HTTPS port number to use. (appears only if HTTPS is among the chosen options).
- Allow Wireless Access - Checking this lets LAN WiFi clients access the web interface via HTTPS. (Default: enabled).
- HTTP and HTTPS - Choosing this allows LAN Ethernet clients to access the web interface via both HTTP and HTTPS protocols.
- HTTP Port - Here, enter the port number on which you want HTTP administration traffic to flow. (Default: 80).
- HTTPS port: Here, enter the HTTPS port number to use. (appears only if HTTPS is among the chosen options).
- Allow Wireless Access - Checking this lets LAN WiFi clients access the web interface. (Default: enabled).
SSL Certificate
Common Name (CN): Here, enter the human-friendly name of the SSL web administrative certificate you wish to generate.
Regenerate:TBD.
Save in NVRAM: TBD.
Remote Access: This lets you choose whether and how a user can remotely access Tomato64's web interface.
- Disabled - This prevents all access to Tomato64's web interface via the WAN port/Internet.
Only LAN clients will be able to access the web interface. For security reasons, this is
the default and recommended setting.
- HTTP - This allows web access to Tomato64's WAN interface/Intenet via the
HTTP web protocol.
- HTTPS - This allows web access to Tomato64's WAN interface/Internet via the
HTTPS (SSL-encrypted web) secure protocol.
Unmount JFFS during upgrade: Checking this unmounts any existing JFFS partition during firmware upgrades. :-(!
Allow Remote Upgrade: Enabling this allows authenticated Internet/WAN clients to perform firmware upgrades via the web interface.
Remote Access: This menu lets you specify which, if any protocols will be allowed when remotely accessing the web interface.
- Disabled - No Remote access to the web interface will be permitted.
- HTTP - Remote access via the HTTP protocol will be permitted.
- HTTPS - Remote access via the HTTPS protocol will be permitted.
Allow Wireless Access: Checking this allows WiFi and Ethernet clients to access the web interface. (Default: Disabled).
Directory with GUI files: Here, select the directory which contains the files that provide the graphical web interface.
CAUTION: Do not change this setting unless you're experienced. An error could prevent you from accessing the web interface.
Theme UI: This lets you choose the color scheme (theme) used for the web interface pages. (Default: Default).
Open Menus: Checking a menu name here will show all its submenus as open. Unchecked menus will display their submenus as nested.
SSH Daemon
Secure SHell is a tunneling protocol that allows you to make secure local and remote connections to the Tomato64 router. With the help of the Dropbear service, it also allows you to make SSH connections though the router, to LAN client devices. Setings in this section let you enable or disable the SSH Daemon and the Dropbear daemon, and configure their operation.
Enable at Startup: Checking this starts the SSH Daemon when the router boots. (Default: Enabled).
Extended MOTD: Checking this enables the Message of the Day function. This function displays a custom message when you first log in via Telnet. The message can be can be important information or updates about the system or just a personal greeting from the system administrator.
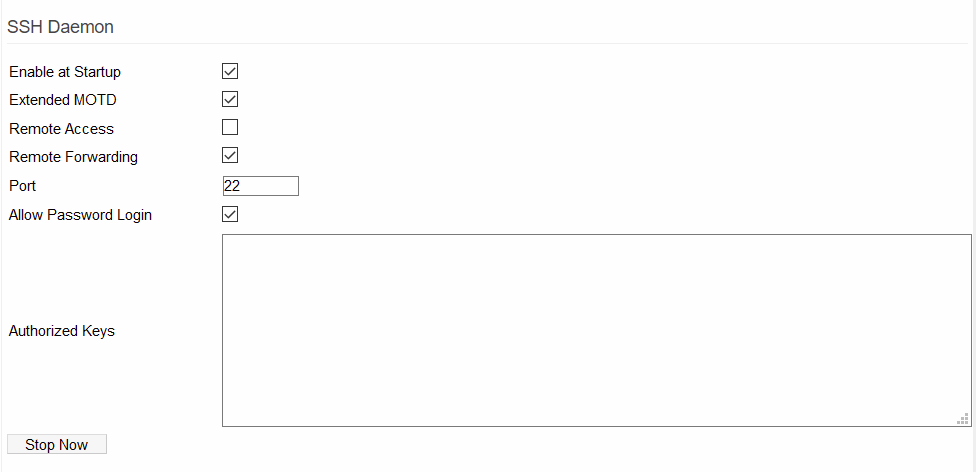
Remote Access: Checking this allows SSH connections from remote WAN/Internet clients. (Default: Disabled).
Remote Forwarding: Checking this enables the Dropbear service. This service/daemon provides SSH services on the router and supports SSH port tunneling/forwarding. Do not confuse this with standard (local) Port Forwarding.
For example, let's say you want to be able to access a Windows PC on your LAN via Remote Desktop, but you don't want the security risk of opening up a port for RDP to the Internet via standard Port Forwarding. Instead, you can make an SSH connection into the router with an SSH port tunnel/forward configured (example: 127.0.0.1:1234 gets tunnelled/forwarded through SSH to 192.168.1.66:3389. This way, when you're connected via SSH to the router, you can open up RDP on the machine running the SSH client, and connect to 127.0.0.1:1234 and you're securely connected to 192.168.1.66 on your LAN. All traffic flows through SSH, and thus is encrypted. (RDP already uses encryption, but it's weaker than that provided by SSH).
Port: Here, enter the port number on which SSH traffic will flow. Changing the port from the default is highly recommended. Port 22 is constantly scanned by Internet hackers. (Default: 22).
Allow Password Login: Checking this allows clients to login via SSH with only the normal administrative username and password. No authorized encryption key is needed. When disabled, SSH will require an authorized key to allow a client to log on.
Authorized Keys: Here enter one or more encryption keys which authorize an SSH client to access to the LAN.
Stop Now: Clicking this button immediately stops the SSH daemon. SSH will start again at the next bootup. After clicking, the button will then display as "Start Now". Clicking it will immediately start the SSH daemon.
Telnet Daemon
(Terminal EmuLation over the NEtwork) is a protocol which allows LAN and remote connections via a command-line interface. Unlike SSH, Telnet is not a secure protocol.
Enable at Startup: Checking this enables the Telnet Daemon, allowing connections to Tomato64 via Telnet.
Port: Here, you can enter the port number on which Telnet connections will be made to the router. (Default: 23).
Stop Now / Start Now. Clicking this button immediately stops the Telnet Daemon. The Telnet daemon will restart at the next reboot (if Enable at Startup is checked). When the Telnet Daemon has stopped, this button will change to read "Start Now". Clicking Start Now immediately starts the Telnet Daemon. When Telnet is finished starting, the text on this button will change back to "Stop Now".

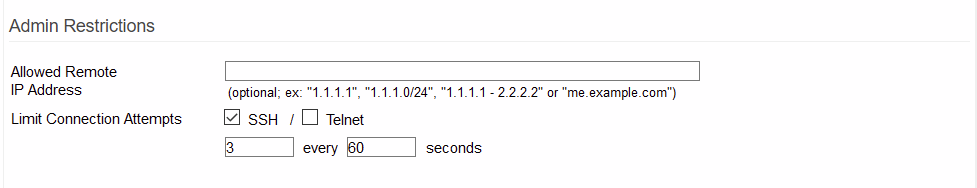
Admin Restrictions
Allowed Remote IP Address: Here, you can specify the IP addresses or DNS names of hosts you want to allow to connect to the Tomato router's web aministration interface. Addresses can be individual, separated with commas, or a range separated by a dash, such as 1.1.1.1-2.2.2.2 . This setting applies to local and remote administration via HTTP, HTTPS, SSH (if enabled) and Telnet (if enabled).
Limit Connection Attempts: Here, you can specify whether you want SSH or Telnet connection attempts to be limited to a certain number of attempts (n) at a certain frequency (f). (Default: 3 connection attempts allowed every 60 seconds).
Checking SSH limits the number of SSH connection attempts to number n at frequency f (in seconds). Checking Telnet limits the number of Telnet connection attempts to number n at frequency s (in seconds).
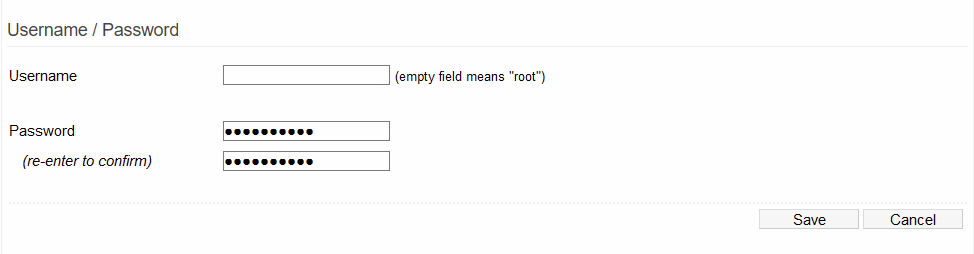
Username/Password
You are strongly urged to change these from the default settings to keep the router and network secure.
Username: Here, enter the Tomato64 logon Username you wish to set. Leaving this field empty sets the username as "root". (Default: "root").
Password: Here, enter the Tomato64 logon password you wish to set. (Default: "admin").
Re-enter to confirm: In this field, enter the password again to confirm it is correct. The password will be changed only when the text entered in this field and in the Password field match exactly.