Advanced-tor: Difference between revisions
(Created page with "<span id="tor"></span> = TOR = <span id="what-is-tor"></span> == What is Tor? == Tor ("The Onion Router") is a security protocol used to increase the anonymity of Internet traffic. Tor's "Onion" routing is implemented at the application layer of the OSI model of the network stack. The TOR network is run as a free, worldwide, volunteer-run overlay network consisting of more than seven thousand relays. When you use the Tor browser, the Tor network do...") |
No edit summary |
||
| Line 35: | Line 35: | ||
<br /> | <br /> | ||
[[File: | [[File:20220126-184923.png|frame|none]] | ||
<br /> | |||
<br /> | <br /> | ||
<br /> | <br /> | ||
| Line 45: | Line 46: | ||
<br /> | <br /> | ||
<br /> | <br /> | ||
[[File: | [[File:20220126-185229.png|frame|none]] | ||
<br /> | |||
<br /> | <br /> | ||
'''Only resolve .onion/.exit domains:''' If this is enabled, only .onion domains will be redirected towards the Tor network. Please Note that you must also enable the <code>Resolve .onion using Tor</code> (assuming Tor is enabled) option in the [[advanced-dhcpdns|DHCP/DNS/TFTP]] menu. | '''Only resolve .onion/.exit domains:''' If this is enabled, only .onion domains will be redirected towards the Tor network. Please Note that you must also enable the <code>Resolve .onion using Tor</code> (assuming Tor is enabled) option in the [[advanced-dhcpdns|DHCP/DNS/TFTP]] menu. | ||
Revision as of 05:37, 30 September 2023
TOR
What is Tor?
Tor ("The Onion Router") is a security protocol used to increase the anonymity of Internet traffic. Tor's "Onion" routing is implemented at the application layer of the OSI model of the network stack. The TOR network is run as a free, worldwide, volunteer-run overlay network consisting of more than seven thousand relays.
When you use the Tor browser, the Tor network does not directly connect your computer to that website. Instead, traffic from your browser is intercepted by Tor and bounced to a random number of other Tor users’ computers before passing the request to its final website destination. The same process is reversed to enable the destination website to communicate with you, the Tor user.
The encryption process that Tor software uses obscures users' identities, requests, communications, and transactions while still enabling them to use the Internet as they normally would.
For more details about how Tor works, please see here: Skerritt Blog: How does Tor Really work?
Limitations
Speed
Encryption, anonymization and multiple hops come at a price. Tor slows your network traffic, since the path that packets take is more complex (circuitous) than with normal traffic. You will probably not want to send interactive traffic over the Tor network. Nor is it recommended that you do heavy downloading (such as Torrents) via Tor. The multiple hops increases latency significantly.
Domain resolution
The Tor network includes its own internal DNS system which is specifically authoritative for the ".onion" domain. This domain exists only within the Tor network. Some modern browsers include built-in functions to resolve ".onion" domains which append ".link" or ".cab" to the ".onion" domain. Check your browser's documentation for details.
TOR Settings
Enable TOR: Checking this enables the Tor client. Be patient. Starting TOR can take from several seconds to several minutes.
Socks Port:
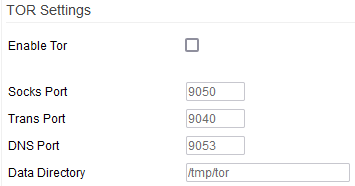
Trans Port: FIXME
DNS Port: FIXME
Data Directory: Here, you can specify where Tor will store its temporary data.
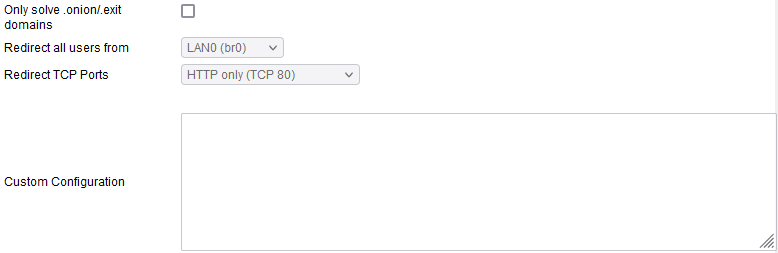
Only resolve .onion/.exit domains: If this is enabled, only .onion domains will be redirected towards the Tor network. Please Note that you must also enable the Resolve .onion using Tor (assuming Tor is enabled) option in the DHCP/DNS/TFTP menu.
- Redirect all users from: **Here, you can specify the source LANs or client IP addresses which will be be permitted to use Tor.
- LANx - Allows you to choose specific subnets whose client devices can access Tor sites.
- Selected IPs - This option lets you specify only certain IP addresses to be allowed to access Tor sites.
Redirect TCP Ports: Narrows down the Tor redirection rule to destination port/s of interest.
- HTTP only (TCP 80)
- HTTP + HTTPS (TCP 80 + TCP 443)
- Selected Ports
Custom Configuration: Here, you can define custom/advanced parameters, as found in the official Tor Documentation.
TOR Notes and Troubleshooting
Warning! If your router has 32MB of RAM or less, you must use swap space on permanent storage to ensure proper functioning.