Restrict: Difference between revisions
(Created page with "<span id="access-restriction"></span> = Access Restriction = The Access Restriction menu contains functions that allow you to block: * Access to the entire Internet. * Access to portions of the the Internet. * WiFi access to the network. Restrictions are done based on rules and a schedule. Access Restriction only blocks traffic routed outbound to the Internet. It '''cannot''' restrict access between (switched) LAN clients. It also cannot block traffic when the device...") |
No edit summary |
||
| Line 32: | Line 32: | ||
<br /> | <br /> | ||
[[File: | [[File:Access restriction overview cropped.png|775px|frame|none]] | ||
<span id="editing-access-restriction-rules"></span> | <span id="editing-access-restriction-rules"></span> | ||
| Line 49: | Line 49: | ||
<br /> | <br /> | ||
[[File: | [[File:Access restriction editing cropped.png|700x593px|frame|none]] | ||
<br /> | <br /> | ||
Revision as of 05:50, 30 September 2023
Access Restriction
The Access Restriction menu contains functions that allow you to block:
- Access to the entire Internet.
- Access to portions of the the Internet.
- WiFi access to the network.
Restrictions are done based on rules and a schedule.
Access Restriction only blocks traffic routed outbound to the Internet. It cannot restrict access between (switched) LAN clients. It also cannot block traffic when the device is used as a switch only or as a wireless bridge. For those scenarios, see the HOWTOs entitled: Wireless MAC filtering via script/scheduler and Block devices via script/scheduler.
Rules can be customized to block:
- Only certain sources
- Only certain destinations
- Only certain ports
- Only certain protocols, or applications
- Only certain HTTP activity
- Combinations of the above
Rules can be edited in the Web interface, and through scripts. Please see the HOWTO entitled: Scripting Access Restrictions.
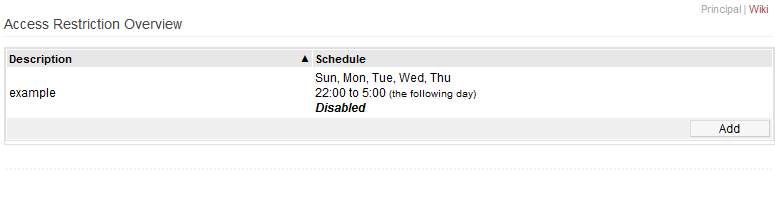
Access Restriction Overview
The table in this section displays all saved rules, both active and inactive.
All rules are listed here. However, adding/editing any rules will forward you to another menu where you can edit the rules.
Editing Access Restriction Rules
After clicking on the Overview table mentioned above, you will be taken to the Rule Editing page.
Here:
- To delete an existing rule, click on it on the Overview page, then in Rule Editing, click Delete.
- To **Edit **an existing rule, click on it on the Overview page, make the changes and click Save.
- To Add a new rule, click the Add button on the Overview page, configure the changes and click Save.
- On the Rule Editing page, sequential rule numbers will display at the top left (For example: ID: 01)
- These numbers will increment by 1 for each new rule you create.
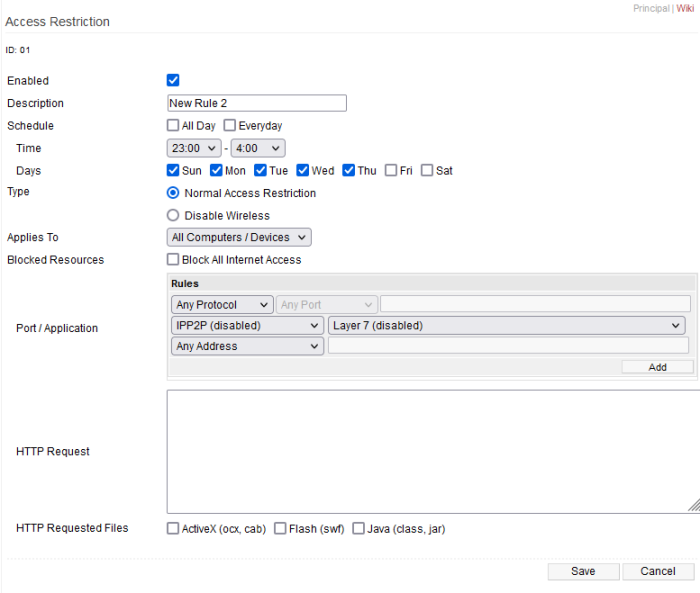
Enabled: Checking this enables this rule.
Description: Here, you enter a name for this rule.
Schedule: Here, you configure the schedule settings for this rule.
- All Day - Checking this applies the rule for the entire day (for all days selected in the Day section).
- Enabling this makes the Time options disappear.
- Every Day - Checking this applies the rule every day.
- Enabling this makes the Days options disappear.
- Time - Here, you set the start time and end time when this rule will be applied.
- Days - Here, you set the Days on which this rule will be applied.
Type:
- Normal Access Restriction - Sets the rule to include all options set below the "Disable Wireless" option.
- Disable Wireless - This rule will disable all WiFi interfaces on the router.
Applies To:
- All Computers/Devices - This rule will apply to all network clients.
- The Following... - This rule will apply to only the specified network clients.
- Add clients by entering their MAC or IP address in the MAC/IP Address field, then clicking Add.
- Clients must be added one at a time.
- All Except... - This rule will apply to all network clients except the one specified.
- You can think of this as somewhat similar to a client whitelist.
- Add clients by entering their MAC or IP address in the MAC/IP Address box, then clicking Add.
- Clients must be added one at a time.
Blocked Resources:
- Block All Internet Access - Enabling this blocks all Internet access to the selected network clients.
Port / Application:
More than one rule can be configured, click the Add button to add a rule.
- Protocol - Choose a protocol to block. Choosing a protocol with fixed ports will grey out the port field.
- Port - Select a source port/destination port in the dropdown. Then, enter the port number in the next box.
- This may be greyed out if you choose a fixed protocol in the Protocol field.
- Application - Select which application to block.
- Address - Select source and/or destination IP address, then enter the IP address in the next field.
HTTP Request:
In this field, you enter the text which will have the Access Restriction in this rule applied to it.
For example:
An entry that contains: "^begins-with.domain"
will block access to any domain that start with the text "begins-with".
An entry that contains: ".ends-with.net$"
will block any domain that ends with "net" .
An entry that contains: "^www.exact-domain.net"$
will block any entry that begins with "www.exact-domain" and ends with ".net"
- HTTP Requested Files: **
This function will block download of certain file types, including the following:
- ActiveX - This will block Windows controls (which usually have a .ocx or .cab file ending).
- Flash (swf) - This option will block Flash .swf files.
- Java (class, jar) - This option will block Java (usually class or .jar) files.
Delete: Deletes the Access Restriction rule displayed on the screen.
Save: Saves the current rule displayed on the screen.
Cancel: Cancels the current rule change(s) or creation, and returns you to the Access Restriction Overview page.